In the name of Allah, the Most Gracious, the Most Merciful.
I. ABSTRACT
In our daily life, many people are often finding some difficulties to manage their financial record. This record generally is about data of income and outcome activities which were in the past or even in the future. In an era which is all about digital like now, manual record is being problem which is hard to be fulfilled. Beside ineffective in recording and searching process, this manual record also has problem to protect itself from being used without permission.
With seeing the need of solving those problems, some developers and even companies are sprung to build and offer many software that help its user to manage their financial record easily. Spending Tracker, Money Monitor, or Pocket Expense are some of the well-known software and placing top for “money” or “account” keyword in Indonesia’s iTunes. Some developers or companies realize the importance of the data and make them offer protection which is considered to protect the user’s confidentiality. Generally, the protection is in the form of PIN or being well-known as Passcode.
Talking about this topic, The Writer will discuss about the safety weakness of Passcode which is offered by “Pocket Expense” (http://www.appxy.com/pocket-expense/) that has reported by The Writer to the developer on July 7th, 2014 GMT+7.
II. INTRODUCTION
Passcode is a need for everyone who wants to protect their confidentiality about something which is considered to be a secret. According to the Oxford Dictionary, Passcode is “A string of characters used as a password, especially to gain access to a computer or smartphone”. In another reference, passcode is a kind of password that is generally used as a mechanism to show identity. Passcode and Password are assessed as something which are made by the user.
In general, the difference between Password and Passcode can be seen from the type of characters that are inputted. If Passcode makes the user must input (only) number, therefore in Password, the user can input a combination of alphabet, number, and symbol.
Then, let’s get to the main topic. Based on the statements above, Pocket Expense is one of the application that offer easiness for their users to manage their financial record. Appxy as the developer also offer the usage of Passcode that only be able for the users who buy the Pro Version of the related application.
Based on the discussion in the Abstract part, in this application, Writer finds that an Attacker can gain Passcode from Pocket Expense application which has been set by the users in order to protect their data. Of course, with using this Passcode, Attacker will be able to login to the related application or even using it to login to the user’s iDevice. Why is this possible? Because generally, someone will use same Passcode as an identification in every systems that have login feature. Moreover, Passcode in Pocket Expense has only 4 digits like iDevice’s which is published by Apple (if the user activates the simple Passcode on their iDevice).
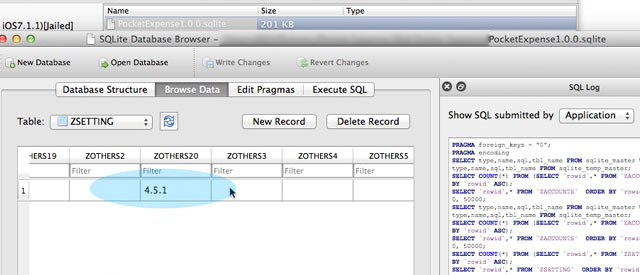
For information, Writer uses Pocket Expense 4.5.1, which is one version late to the version 5.2.1 which has been published by Appxy after the Writer submitted the vulnerability of the Passcode.
III. AFFECTED VERSION AND CONDITION
The version of Pocket Expense which is having vulnerable security is the 4.5.1 version. Here are the conditions that allow the Attacker to read the Passcode from Pocket Expense:
- iDevice isn’t need to be in jail-break condition (remember, below of iOS 8.3, we still able to accessing the Sandbox of the App without Jailbreak).
- iDevice isn’t need to be in standby condition. In other words, this gap can also being used even the iDevice is in locked condition with the Passcode for that iDevice itself (as long the device is trusted by the Desktop OS that we would like to use).
- Writer tries it in Pocket Expense for iPhone and iPad with 6.1.3 and 7.1.1. iOS version.
IV. PROOF OF CONCEPT
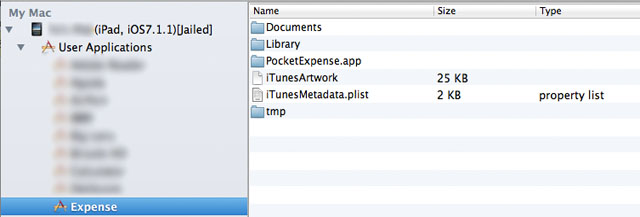
1. Connect the iDevice which has Pocket Expense in it with PC.
2. Access the “Applications” directory in iDevice with iExplorer tools, like iFunBox.
3. Go to the “Expense” application.
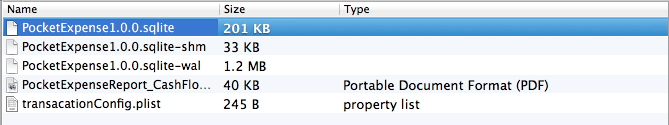
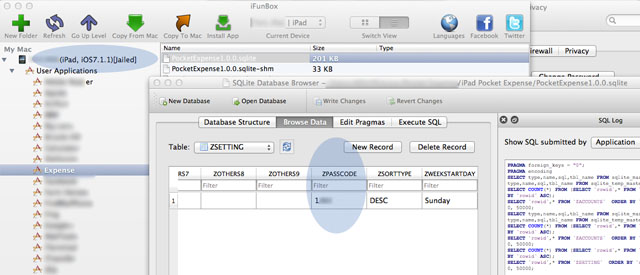
4. Go to the “Documents” directory and we’ll see some files. One of them is a file with ‘sqlite’ format.
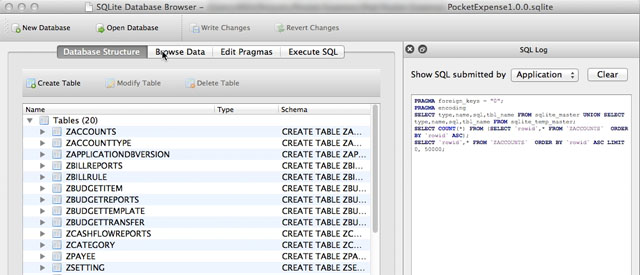
5. Open “PocketExpense1.0.0.sqlite” file with SQLiteBrowser or such.
6. After that, access the “ZSETTING” table and pay attention to the “ZPASSCODE” part. You will see that this “Passcode” which is used to protect the data from Pocket Expense is being saved in plaintext and can be accessed even the iDevice isn’t in jail-break condition.
V. RESPONSE FROM DEVELOPER
There has been no responses from the developer side to the e-mail that contains vulnerability from Pocket Expense application which is sent by The Writer on July 7th, 2014. However, uniquely the developer side has fixed and updated their both applications (for iPhone and iPad) in App Store on July 16th, 2014. The most disappointing thing is, the user which has paid for 4.5.1 version doesn’t get the update to the related vulnerability and even this version has been removed by the developer. In other words, user has to buy the application that has been updated to the 5 version one more time.
However, the positive thing of this is the user doesn’t need to worry about the problem anymore.
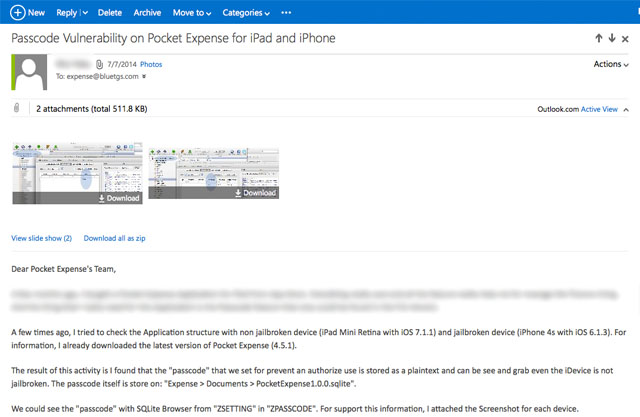
VI. SUMMARY AND RECOMMENDATION
Generally, with using these vulnerabilities, the Attacker will absolutely gain access to the data which is saved in the related application. Besides that, these vulnerabilities can also harm the iDevice user that is accustomed to equate the value of the Passcode.
As example, Passcode that is used by user in this Pocket Expense application is 5566. It’s not impossible for the users to use the same simple Passcode for their iDevice, which means it can be resulted in misuse and brings greater impacts.
With seeing the status related to this, so the recommendations which can be implemented by the users if they won’t buy the newest version of this application, are:
- Turning off the “simple passcode” feature if the users are more accustomed to use one kind of combination for every identities.
- If the users still want to use the “simple passcode”, so the users are recommended to differentiate the Passcode that is used to login to the iDevice with the Passcode that is used to login to the Pocket Expense application.
And if the users don’t mind to buy the newest version, of course the vulnerabilities aren’t being worries anymore, considering that the Pocket Expense no longer use the “Passcode” value according to the description in this simple paper.
VII. ADDITIONAL INFORMATION
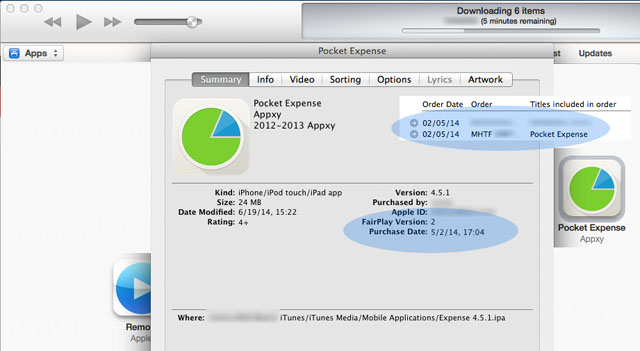
1. Writes used the Paid – Pocket Expense with 4.5.1 version for iPad and iPhone that the Writer bought from App Store back in the May, 2014.
2. The logo color of the Paid- Pocket Expense is differentiated to the free one. If the free one has red logo, the paid one has blue logo.
3. Paid- Pocket Expense for iPad (v.4.5.1) hasn’t got update anymore. This thing can be seen by opening our software list in iTunes software and accessing Pocket Expense in App Store through the downloaded list.
4. Writer doesn’t know the exact release schedule of the 5th version, because according to the 5th paid version in App Store, the release schedule was in May, 2014. However the reparation for the free version is shown on July 16th, 2014 which is updated from the v.4.5.1 to the 5th version.
Please kindly visit this simple paper directly to looking this release in simple:
• [English Version] Insecure Data (Passcode) Storage at Pocket Expense for iOS version <= 4.5.1 (translated by vky[at]firstsight.me)
• [Indonesian Version] Insecure Data (Passcode) Storage at Pocket Expense for iOS version <= 4.5.1